PIERCE COUNTY, Wash. — For the first time since the Clover Park School District was possibly taken over by a ransomware attack, the hackers have claimed to release information taken from the district.
In a new series of webpages, the hackers list Clover Park School District as one of multiple agencies and organizations they have infiltrated. Other victims include official county websites in Illinois and Alabama.
A statement on a page dedicated solely to the Clover Park School District reads, “The network of Clover Park School District was screwed and now we have about 5 GB data from file servers, including internal company documents, personal and customers data. According to our rules we are publishing this data step by step in case if this company will keep silence.”
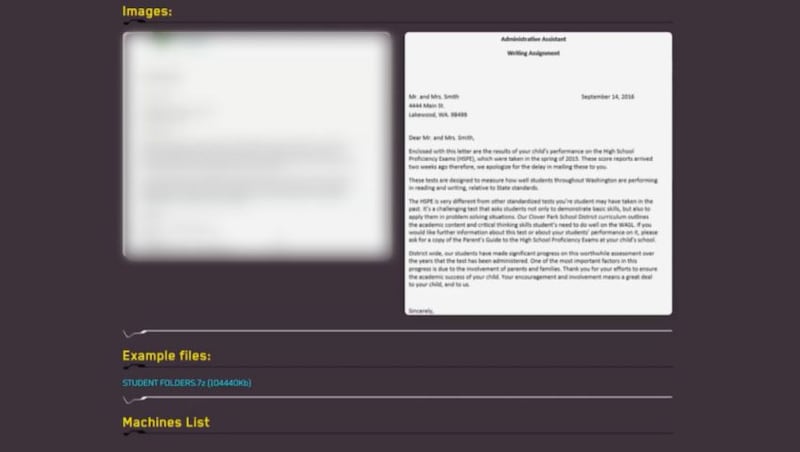
Another webpage shows two images and provides a download link, which is a zip file containing student assignments and presentations. The first image shows a letter sent from the district’s human resources department to a former employee. The letter informs the employee they are under investigation and being placed on administrative leave. The second image shows a letter informing “Mr. and Mrs. Smith” of their child’s grades, including an address for 4444 Main Street in Lakewood. That address does not exist, according to Pierce County property records.
The district responded to the images with the following statement:
“We are aware of the online posting. We are working with third-party specialists to complete our ongoing investigation to determine the full nature and scope of this event. If we determine that the event impacted personal information, we will move as quickly as possible to notify individuals. Protecting the privacy of our students, staff, and faculty and ensuring the security of information stored on our systems remains one of our highest priorities.”
In a public statement released Tuesday, the district stated:
“CPSD is operating on regular schedule tomorrow, Tuesday, June 1. Staff will report to work in alignment with reporting requirements. On Tuesday morning, students will have access to their classroom teams and district learning apps.
“We’ve created a temporary district website that we are adding content to: https://cpsd.cloverpark.k12.wa.us/
“Our district is working with third-party cybersecurity experts to address the malware event and will keep staff and families informed. We appreciate your patience and support as we move to restore systems as quickly as possible.”
Scroll down to continue reading
More news from KIRO 7
- Charges filed in death of WSU fraternity pledge
- Woman accidentally shoots 5-year-old son while trying to shoot dog, reports say
- Officials investigate Shoreline burger restaurant for outbreak of norovirus-like illness; 23 sickened
- Do you have an investigative story tip? Send us an email at investigate@kiro7.com
Multiple cybersecurity experts, including Brett Callow, believe the district is going through a ransomware attack.
“I look at the threat landscape and try to deduce what may be coming next in order to protect our customers against it,” Callow, a threat analyst with Emsisoft, said. “Typically, ransomware groups start by posting the least sensitive information first. That way, they’re not removing any incentive from the organization to pay to prevent the remaining data being published. But what may actually be in those files would be impossible to know.”
Callow said any ransomware hack includes two issues: First, locking an organization out of an operating system. Secondly, hackers will threaten to release or publish any stolen data.
Callow said solving the first issue can be done in the same way Clover Park School District did by creating an entirely new website. The district also stated it plans to launch an entirely new website in the fall.
The harder problem to solve is the second one, Callow said, because information is impossible to refund or take back.
“It’s bad, bad stuff. At least if your financial information is compromised, you can eventually fix the credit. If information along those lines leaks, there’s nothing you can do once it’s out there. Once it’s out there, it’s out there forever,” Callow said. “Really, organizations in this situation have no good option. If they refuse to pay, then whatever data was stolen will be posted online. If they do pay, they’ll simply receive a pinkie promise from the criminals that the stolen data will be destroyed.”
Callow said the best thing organizations and companies can do is “pay attention to the basics,” including using multi-factor authentication for logging into operating systems. He also believes ransomware attacks will continue to increase as time goes on.
“The perpetrators, at the moment, have a near-zero chance of being caught. The effect of prosecution rate for cybercrime in the U.S. is currently at .05%. So the criminals really are operating on almost complete impunity, and there is no reason why the attacks should stop,” Callow said. “I think a lot of people don’t realize just how common these hacks are. ... They will stop only when they cease to be profitable.”
©2021 Cox Media Group